In Network Security Operations, What You Don’t Know Will Hurt You
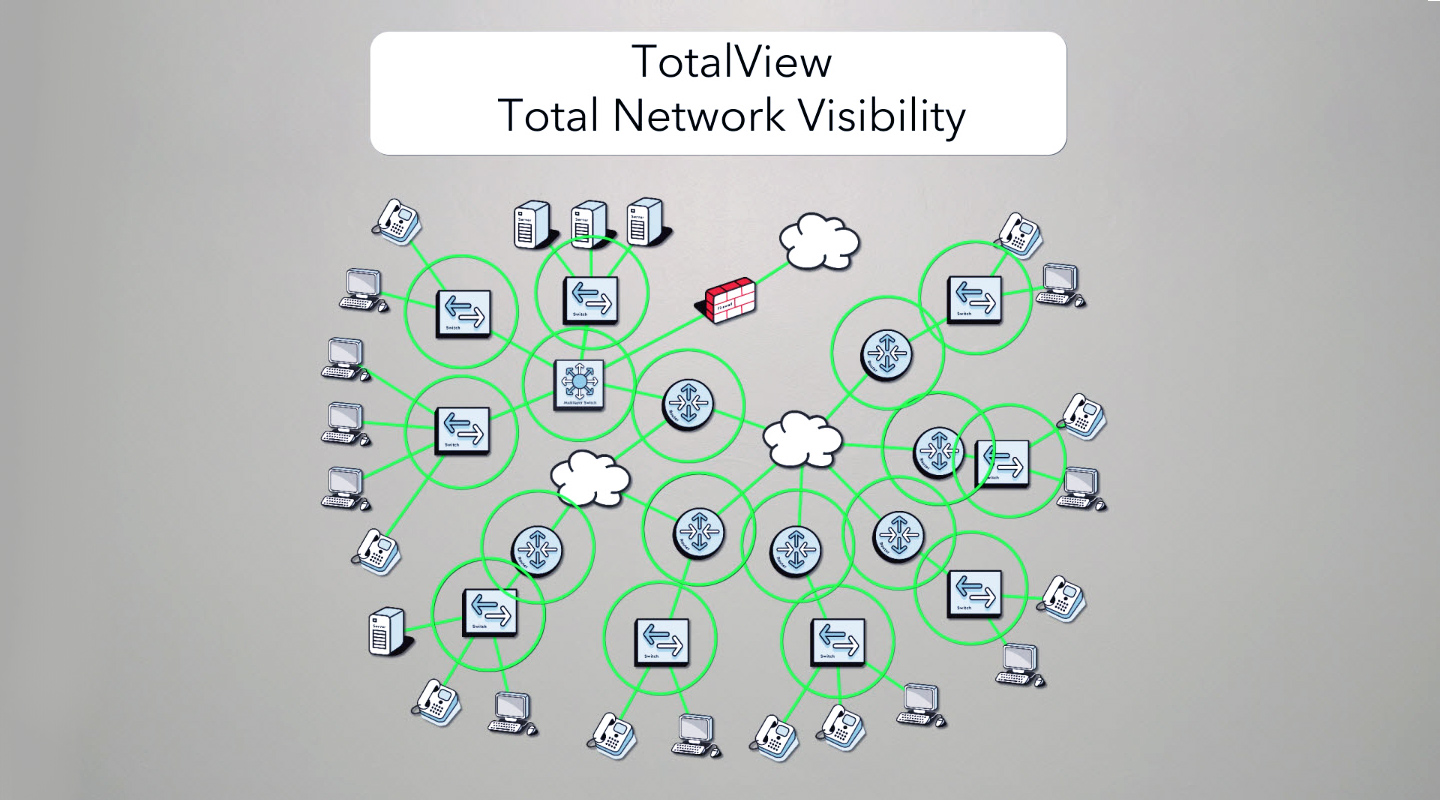
TotalView® Security Operations Manager is all about giving you Total Network Visibility into the security of your network environment.
If you knew what was on your network, where devices are connected, who is logged in, what they are doing, who they are communicating with, and the risks of that communication, you can quickly make informed decisions if the activity is appropriate, and quarantine the computer if not.
This is what TotalView Security Operations Manager is designed to do: Create awareness of what’s happening on your network and where your data is going, manage risks and also comply with data sovereignty policy requirements
Event Response Optimization
Event Response OptiTotalView Security Operations Manager has all of the enrichment capabilities to quickly research a security event and determine where the device is connected to the network (Switch, port, and VLAN), what the device is, who is logged in, what processes they are running, who they are communicating with, where the data is going, the risks associated with those communications, and then quarantine the computer.
Your SIEM may generate hundreds of false positive alerts, that someone needs to research and follow up on, to ensure that real threats get appropriately addressed. If your current process requires 30 minutes of playbook execution with a wide variety of tools, a single analyst might only be able to research 20 events per day. This can be a very inefficient and ineffective approach to addressing potentially catastrophic events.
All of this capability built into one solution means security event research and playbook execution is now a 5-minute exercise.
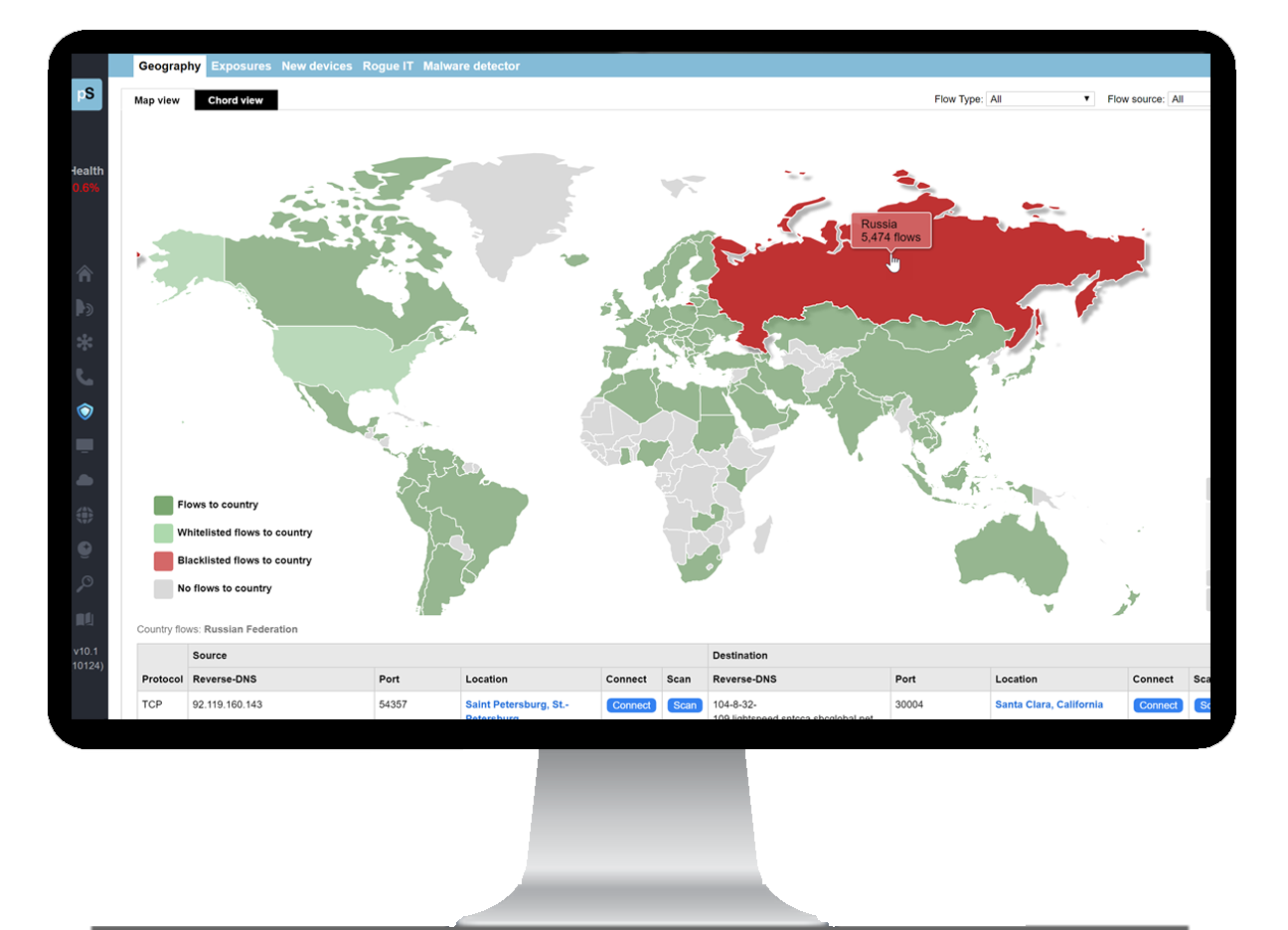
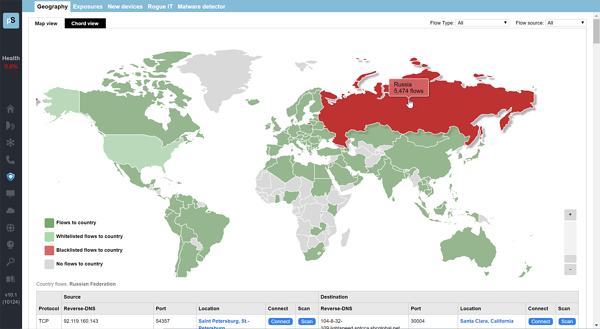
Geographic Risk Management
Our solution allows you to manage the risks associated with data crossing international borders: In today’s hostile cyber environment, it is essential that you have geographic awareness of your data. Data exfiltration, including the loss if intellectual properly, can be detrimental to your business. You’ll knew at a glance which countries your data is going to, and the risks associated with those communications.
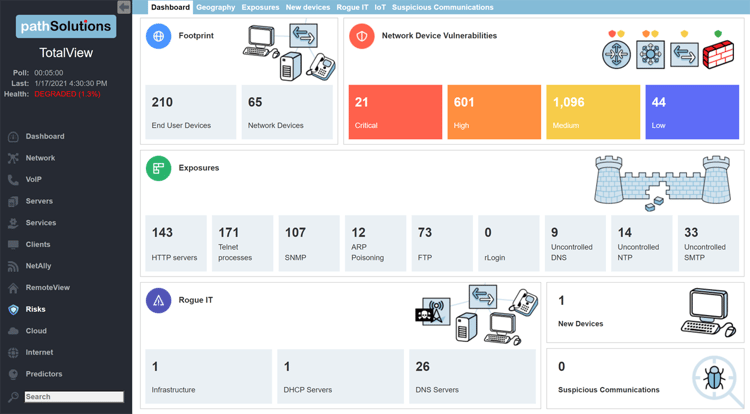
Infrastructure Vulnerability Detection
Scanning for network device vulnerabilities can be tedious and time consuming but is an essential part of maintaining strong cyber hygiene. TotalView Security Operations Manager automates this activity and rapidly discloses vulnerabilities for all infrastructure devices in your network. Daily NIST.gov checkups with the NVD means you will always know what CVE IDs are relevant to your equipment so remediation efforts can be undertaken rapidly.
Rogue IT Device Detection
If a Rogue network switch, AP, DHCP or DNS server was connected to your network, how fast could you locate the switch and port where it is connected and quarantine it? Since TotalView Security Operations Manager knows what’s connected to your network, and what traffic each device sends/receives, it can easily and rapidly identify these devices to help protect against these exposures.
New Device Detection
When a mystery device shows up on the network, can you identify where it is, what it is, and who it is communicating with? TotalView Security Operations Manager covers this base so you can have complete awareness of what is on your network and who is talking to whom.
IoT Device Tracking
All of your IoT devices are automatically found and listed on the IoT tab. Printers, card access systems, webcams, HVAC control systems, and other IoT devices will show where they are connected (switch, port, VLAN). You can easily determine how to connect to the device with the mini port-scanner which will allow you to connect to it via Telnet, SSH, HTTP, or HTTPS. Thus, you can find where these devices are, what they are, as well as whom they communicate with. IoT devices are notorious for not having default username and passwords turned off. With TotalView Security Operations Manager, you can quickly identify this vulnerability and take action to protect against a compromise.
Exposure Reporting
Do you know if bad network security practices are in use in your organization? Unencrypted protocols like Telnet, HTTP, rlogin, and FTP may exist in places that you might not be aware of. Uncontrolled DNS, NTP, and SMTP creates a lot of exposures. When poor security practices are implemented, exposures get created. We can instantly show you where these bad practices originate from so overall risk can be reduced.
Communications Policy Monitoring
With TotalView Security Operations Manager, you can set up security communications policies that can make sure you are aware of policy violations.
If you have a high-security database, you can create a policy that permits only the App servers, backup server, and DBA to talk to the database. If anyone outside of that group attempts to talk to the database, a policy violation alert will be generated.

Pivot Detection
When tracking down a suspicious device, you can see who it has been communicating with. If it has been communicating with a known threat actor, you can instantly see who else has been communicating with that actor, and rapidly determine how far the exposure has gone.
Suspicious Communications Detection
TotalView Security Operations Manager downloads a comprehensive blacklist of malware and SPAM sources every 24hrs and identifies communications involving untrustworthy hosts. Alerts can be triggered so if any unsavory communications occurs you can immediately act on it.
Attack Surface Vulnerability Detection
If you learn of a brand-new vulnerability with a webcam manufacturer, how fast can you discover if any exist on your network? If they are present, how fast can you learn where and how they are connected, and if they are running the susceptible code? Can you rapidly quarantine them? TotalView Security Operations Manager has all of this capability so response can be rapid.