 The American Heritage Dictionary defines a squatter as one who settles on unoccupied land without legal claim.
The American Heritage Dictionary defines a squatter as one who settles on unoccupied land without legal claim.
We are entering a new age where network squatters are slowly creeping into enterprise networks, yet network professionals are unaware of the problem.
What Is an OUI?
When a manufacturer decides to add an Ethernet adapter or wireless adapter to their device, the typical process involves paying the IEEE for a MAC address OUI (Organizationally Unique Identifier). The IEEE will then assign the OUI to the manufacturer, and the manufacturer can then use all MAC addresses that start with that three-octet prefix.
For example, if the IEEE assigned 01-4F-89 to your company, you could then assign your adapters with any address between:
01-4F-89-00-00-00
and
01-4F-89-FF-FF-FF
That gives you over 16 million MAC addresses that you can use. If your company has plans to ship more than 16 million adapters, then you have to go back and buy more OUI assignments from the IEEE.
What Is Being Squatted?
With the proliferation of IoT devices, there are thousands of new manufacturers that have popped into existence. Many of these companies have little networking experience, along with little working capital. As a result, they may decide to not pay the IEEE for an OUI allocation and will just start using an OUI that is currently unused.
How Do Network Squatters Hurt Operations?
This creates two problems for network engineers:
- Network engineers cannot easily identify the device manufacturer on their network. If the OUI is “unknown”, then the ARP caches must be queried to determine the IP address of the device, then must initiate a port scan to determine how the device communicates, then attempt to connect to the device to learn what its purpose/function is.
-
The MAC address may eventually conflict with others on the network. If the IEEE assigns the OUI to a different company (perhaps a year or two down the road), the MAC addresses may conflict with the previously deployed devices. The odds of this happening may be low, but if all IoT devices are relegated to an IoT VLAN, the chances increase of having strange operating characteristics:
- Some devices seem to work then fail due to switches seeing the same MAC address on different interfaces.
- STP topology resets may also occur
What Can Be Done to Help?
TotalView’s IoT reporting can automatically identify where these devices are connected, and also show how they are managed so it’s easy to determine the device’s function and purpose. IoT device security is included in the security features of TotalView 10.
Figure 2. IoT Device Security Tab
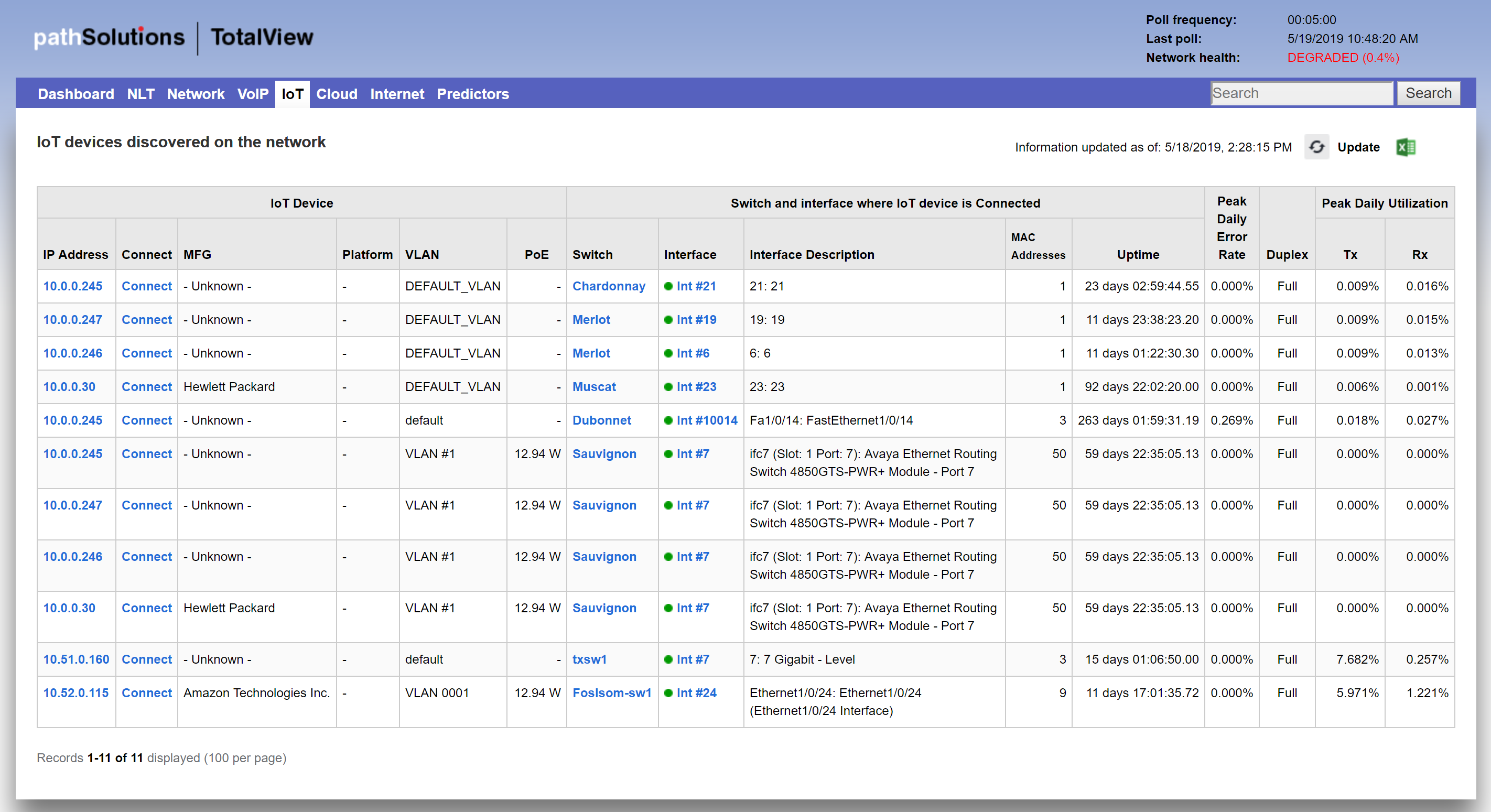
Network troubleshooting problems can be prevented if the right information is brought to bear about your network’s performance and configuration.
Review our white paper or contact us with questions about how PathSolutions TotalView can make network troubleshooting easier.






