 If one of your servers or workstations were sending data to a server in Russia, would you know it?
If one of your servers or workstations were sending data to a server in Russia, would you know it?
Many organizations operate where they trust outbound communications from clients because they are being initiated from presumed "secured" clients.
The problem is with the presumption that the clients are secured—if even a single client starts to communicate with a server located in a questionable country, security may be compromised as data may be exfiltrated without knowledge, or a bot might be added through a browser vulnerability.
How do you track these sorts of communications easily?
Adding Security Visibility
If you track NetFlows through the network, and perform lookups of the city, state, and country where an external IP address resides, you can know where your data is flowing to/from.
In an ideal world, you would want to know if an IP address is flagged by ISPs as suspicious, used for Tor servers on the Dark Web, or a hack source.
If you have a NetFlow collector, you can review the IP addresses of remote public endpoints to learn a lot about the server or service that is being communicated with.
Here are information services that you can use to collect intelligence relating to an IP address:
- IANA (Internet Assigned Numbers Authority) tracks who owns/manages each IP address on the Internet. Depending on the IP address range, it may be sub-managed by a Regional Internet Registry (RIR):
- AFRINIC – Africa Region
- APNIC – Asia/Pacific Region
- ARIN – Canada, USA, and some Caribbean Islands
- LACNIC – Latin America and some Caribbean Islands
- RIPE NCC – Europe, the Middle East, and Central Asia
- Reverse DNS (rDNS) lookup services can be used to lookup the name for any IP address. Most IP addresses will have a reverse DNS name that discloses the domain owner or manager of the IP address.
- IP address geolocation services can be used to determine the location of individual IP addresses and also show security risks associated with certain IP addresses.
Automating Security Visibility
TotalView wraps all of the above capabilities into a single solution that will show you the flows that a desktop or server has communicated with, and the location and security risk for each external flow.
For example, it is easy to see in the report below that a flow is communicating with a server in North Korea, and the event is flagged in red as a hack source with a high risk threat level:
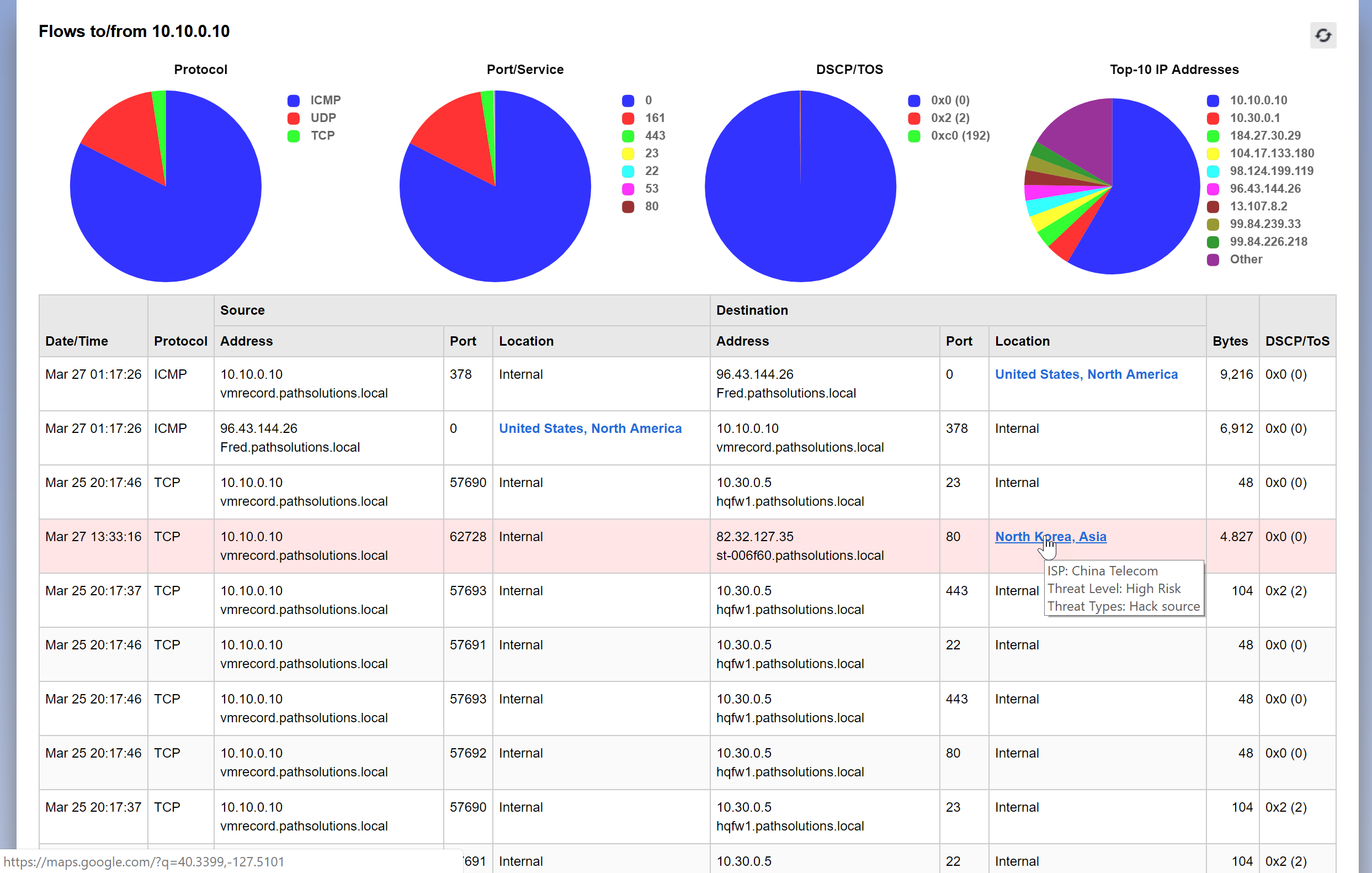
Awareness of your network devices' communications and their destinations is crucial to tracking where data is going, and who is getting control of it
Network security and awareness problems can be prevented if the right information is brought to bear about your network's operations.
Contact us with questions about how PathSolutions TotalView can make understanding your network easier.
See Also
- The Vulnerable Underbelly of Your Network
- IoT Device Security and Monitoring
- Network OUI Squatters and IoT Devices
Sources
- "China, Russia Biggest Cyber Offenders: A new study attributes more than 200 cyberattacks to the two countries over the past 12 years." USNews.com
- "Significant Cyber Incidents Since 2006." CSIS.org






